kerberos smart card authentication These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details . Discover V1CE’s full range of NFC products, from NFC business cards to .
0 · what is kerberos pre authentication
1 · what is kerberos based authentication
2 · kerberos authentication troubleshooting guidance
3 · kerberos authentication step by
4 · kerberos authentication how it works
5 · kerberos authentication guide
6 · kerberos authentication diagram
7 · explain the authentication standards kerberos with suitable diagram
Today, we’re going to show you how easy it is to make an RFID clone and an NFC clone, talk about the best ways to thwart black hats that are after your cards, as well as touch .Most of the time these NFC cards are using encryption so it is not possible to emulate them .
Remote Desktop Services enables users to sign in with a smart card by entering a PIN on the RDC client computer and sending it to the RD Session Host server in a manner similar to .These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details .When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a . In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol.
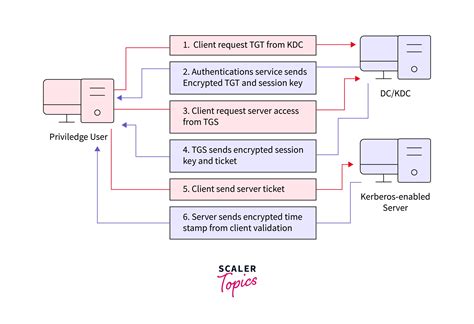
Kerberos, on the other hand, also accepts KERB_SMART_CARD_LOGON and KERB_CERTIFICATE_LOGON formats. And that's where the authentication via a physical device, such as a smart . Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is .Kerberos is an authentication protocol significantly safer than normal password-based authentication. With Kerberos, passwords are never sent over the network, even when .Smart cards can be used with Kerberos, but it requires additional configuration to recognize the X.509 (SSL) user certificates on the smart cards: Install the required PKI/OpenSSL package, .
Kerberos sends a request to the Kerberos Distribution Center (KDC) on the domain controller for authentication. The request includes a copy of the x.509 certificate (from the . If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware.Remote Desktop Services enables users to sign in with a smart card by entering a PIN on the RDC client computer and sending it to the RD Session Host server in a manner similar to authentication that is based on user name and password.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
what is kerberos pre authentication
When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a PIN, which is then sent to the smart card.
In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol. Kerberos, on the other hand, also accepts KERB_SMART_CARD_LOGON and KERB_CERTIFICATE_LOGON formats. And that's where the authentication via a physical device, such as a smart card, or an external web server comes into play.
Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter.Kerberos is an authentication protocol significantly safer than normal password-based authentication. With Kerberos, passwords are never sent over the network, even when services are accessed on other machines.Smart cards can be used with Kerberos, but it requires additional configuration to recognize the X.509 (SSL) user certificates on the smart cards: Install the required PKI/OpenSSL package, along with the other client packages: [root@server ~]# yum install krb5-pkinit. Kerberos sends a request to the Kerberos Distribution Center (KDC) on the domain controller for authentication. The request includes a copy of the x.509 certificate (from the smart card).
what is kerberos based authentication
If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. Virtual smart cards were introduced to alleviate the need for a physical smart card, the smart card reader, and the associated administration of that hardware.
Remote Desktop Services enables users to sign in with a smart card by entering a PIN on the RDC client computer and sending it to the RD Session Host server in a manner similar to authentication that is based on user name and password.These Windows Domain configuration guides will help you configure your Windows network domain for smart card logon using PIV credentials. There are many useful pages and technical articles available online that include details on configurations and using generic smart cards.
hp smart card terminal keyboard price
When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a PIN, which is then sent to the smart card. In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol.
Kerberos, on the other hand, also accepts KERB_SMART_CARD_LOGON and KERB_CERTIFICATE_LOGON formats. And that's where the authentication via a physical device, such as a smart card, or an external web server comes into play. Authentication is a process for verifying the identity of an object or person. When you authenticate an object, such as a smart card, the goal is to verify that the object is genuine. When you authenticate a person, the goal is to verify that you aren't dealing with an imposter.Kerberos is an authentication protocol significantly safer than normal password-based authentication. With Kerberos, passwords are never sent over the network, even when services are accessed on other machines.
Smart cards can be used with Kerberos, but it requires additional configuration to recognize the X.509 (SSL) user certificates on the smart cards: Install the required PKI/OpenSSL package, along with the other client packages: [root@server ~]# yum install krb5-pkinit.
kerberos authentication troubleshooting guidance
kerberos authentication step by
kerberos authentication how it works
kerberos authentication guide

Wood NFC Business Cards. White Oak Wood Business Cards. Order Process STEP 1 | ORDER. Pick your product, select the quantity and configure the product by uploading your own drawings, logos, or even a picture of your current card, and note any content and ideas for your design. Then, place your order through our secure website.
kerberos smart card authentication|kerberos authentication troubleshooting guidance